If you are writing code, you need SSL for development. You can self-sign a “fake” certificate, but you will always get browser warnings.
Not anymore!
mkcert is an excellent tool to create and trust locally SSL certificates for software development.
Setup
Actually, no setup is required. mkcert is a binary file available for any Operating System. You can put it in a directory and run it from there.
In my case: My workstation runs Xubuntu and I will put mkcert in /data/apps folder.
Download pre-built binaries from https://github.com/FiloSottile/mkcert/releases
The latest version (at this time) is v1.4.2
mkdir -p /data/apps/mkcert
cd /data/apps/mkcert/
wget https://github.com/FiloSottile/mkcert/releases/download/v1.4.2/mkcert-v1.4.2-linux-amd64
Make it executable
chmod +x /data/apps/mkcert/mkcert-v1.4.2-linux-amd64
Create a shortcut mkcert to execute the program
cd /usr/local/bin
sudo ln -s /data/apps/mkcert/mkcert-v1.4.2-linux-amd64 mkcert
On Linux, install certutil
sudo apt-get install libnss3-tools
Create Local Certificate Authority (CA)
Your Local Certificate Authority is created only the first time (once):
mkcert -install
Created a new local CA at "/home/pontikis/.local/share/mkcert" 💥
The local CA is now installed in the system trust store! ⚡️
The local CA is now installed in the Firefox and/or Chrome/Chromium trust store (requires browser restart)! 🦊Create SSL
Example: Create and trust (locally) the domain dev.medisign.docker
First make the available changes to /etc/hosts for example:
172.18.0.10 dev.medisign.docker
Then create the local certificate
mkcert dev.medisign.docker
Using the local CA at "/home/pontikis/.local/share/mkcert" ✨
Created a new certificate valid for the following names 📜
- "dev.medisign.docker"
The certificate is at "./dev.medisign.docker.pem" and the key at "./dev.medisign.docker-key.pem" ✅Put the .pem files somewhere in your server (in my case at /etc/ssl-dev) and make the appropriate changes in webserver (Apache in my case) setup
Something like this:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName dev.medisign.docker
ServerAdmin you@your-gmail.com
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile /etc/ssl-dev/dev.medisign.docker.pem
SSLCertificateKeyFile /etc/ssl-dev/dev.medisign.docker-key.pem
</VirtualHost>
</IfModule>
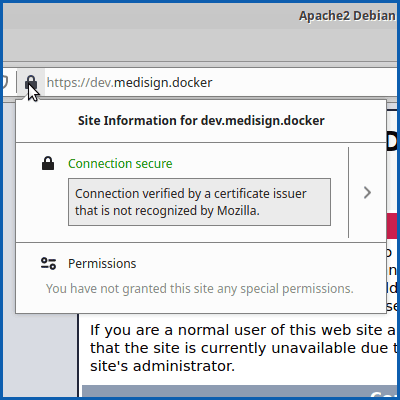
As you can see, SSL are considered valid either from Google Chrome
or from Firefox
Make the certs valid in other trusted machines
Sometimes you need your local domains (and SSL certificates) to be available on your laptop or a docker container. Or you need to use them after you set up your workstation with a new O/S version.
Find rootCA.pem using
mkcert -CAROOT
result
/home/pontikis/.local/share/mkcert
Copy rootCA.pem to relevant path in trusted machine and simply run
mkcert -install
Using the local CA at "/home/pontikis/.local/share/mkcert" ✨
The local CA is now installed in the system trust store! ⚡️
The local CA is now installed in the Firefox and/or Chrome/Chromium trust store (requires browser restart)! 🦊Important Security Notice
Warning: the file rootCA-key.pem that mkcert automatically generates, gives complete power to intercept secure requests from your machine. Do not share it in untrusted machines.
Entrepreneur | Full-stack developer | Founder of MediSign Ltd. I have over 15 years of professional experience designing and developing web applications. I am also very experienced in managing (web) projects.